Transform() 함수 내부에서 동작하는 여러 모듈들..
RR(Rotate Right)
* RTL
// rotate right
module calc_RR(
input wire [8*8-1:0] x,
input wire [4:0] n,
output wire [8*8-1:0] calc_x
);
assign calc_x = (x>>n) | (x<<(64-n)); // 64bit
endmodule(x>>13) | (x<<(64-13))
= (x>>13) | (x<<51)
* TestBench
`timescale 1ns/1ps
module tb_define;
reg [8*8-1:0] i_msg;
reg [4:0] i_cnt;
wire [8*8-1:0] o_result;
calc_RR U0_RR (
.x ( i_msg ),
.n ( i_cnt ),
.calc_x ( o_result )
);
// Generate inputs
initial begin
i_msg = 'b1100_1100;
i_cnt = 'd13;
#(50);
$finish;
end
endmodule
출력 결과


13회 오른쪽으로 회전 이동을 한 결과이다.
입력값: 0000_0000_0000_0000__0000_0000_0000_0000__0000_0000_0000_0000__0000_0000_1100_1100
출력값: 0000_0110_0110_0000__0000_0000_0000_0000__0000_0000_0000_0000__0000_0000_0000_0000
x>>13 : 0000_0000_0000_0000__0000_0000_0000_0000__0000_0000_0000_0000__0000_0000_0000_0000
x<<51 : 0000_0110_0110_0000__0000_0000_0000_0000__0000_0000_0000_0000__0000_0000_0000_0000
-------------------------------------------------------------------------------------------------------------------------------------
or연산 : 0000_0110_0110_0000__0000_0000_0000_0000__0000_0000_0000_0000__0000_0000_0000_0000
Sigma0, Sigma1
* RTL
module Sigma0(
input wire [8*8-1:0] x,
output wire [8*8-1:0] calc_x
);
wire [4:0] n0;
wire [4:0] n1;
wire [4:0] n2;
wire [8*8-1:0] calc_x0;
wire [8*8-1:0] calc_x1;
wire [8*8-1:0] calc_x2;
assign n0 = 'd2;
assign n1 = 'd13;
assign n2 = 'd22;
calc_RR U0_RR (
.x ( x ),
.n ( n0 ),
.calc_x ( calc_x0 )
);
calc_RR U1_RR (
.x ( x ),
.n ( n1 ),
.calc_x ( calc_x1 )
);
calc_RR U2_RR (
.x ( x ),
.n ( n2 ),
.calc_x ( calc_x2 )
);
assign calc_x = calc_x0^calc_x1^calc_x2; // XOR
endmodule※ Sigma1는 Sigma0의 코드에서 아래의 코드 부분만 다르다.
assign n0 = 'd6;
assign n1 = 'd11;
assign n2 = 'd25;
* TestBench
`timescale 1ns/1ps
module tb_Sigma0;
reg [8*8-1:0] i_msg;
wire [8*8-1:0] o_result;
Sigma0 U0_SIGMA0(
.x ( i_msg ),
.calc_x ( o_result )
);
// Generate inputs
initial begin
i_clk = 1'b1;
i_msg = 'b1100_1100;
#(10);
$display("o_result = '0x%b'", o_result);
#(50);
$finish;
end
endmodule
출력 결과
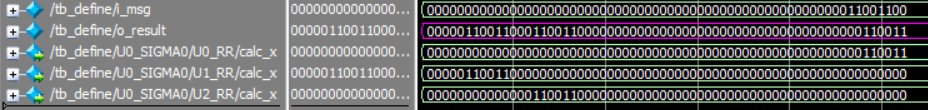
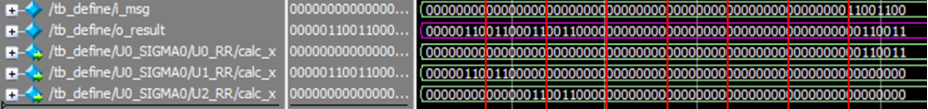
입력값: 0000_0000_0000_0000__0000_0000_0000_0000__0000_0000_0000_0000__0000_0000_1100_1100
출력값: 0000_0110_0110_0011__0011_0000_0000_0000__0000_0000_0000_0000__0000_0000_0011_0011
RR(x, 2) : 0000_0000_0000_0000__0000_0000_0000_0000__0000_0000_0000_0000__0000_0000_0011_0011
RR(x, 13) : 0000_0110_0110_0000__0000_0000_0000_0000__0000_0000_0000_0000__0000_0000_0000_0000
RR(x, 22) : 0000_0000_0000_0011__0011_0000_0000_0000__0000_0000_0000_0000__0000_0000_0000_0000
-------------------------------------------------------------------------------------------------------------------------------------
xor연산 : 0000_0110_0110_0011__0011_0000_0000_0000__0000_0000_0000_0000__0000_0000_0011_0011
'Hardware Security' 카테고리의 다른 글
| [SHA256] FF 모듈 (0) | 2022.02.23 |
|---|---|
| FF 구성 모듈 (0) | 2022.02.17 |
| RR(Rotate Right) (0) | 2022.02.04 |
| [SHA256][Verilog HDL] 코드 만들기 (0) | 2021.11.18 |
![[SHA256] FF() 구성 모듈 - (1): RR, Sigma0, Sigma1](https://img1.daumcdn.net/thumb/R750x0/?scode=mtistory2&fname=https%3A%2F%2Fblog.kakaocdn.net%2Fdn%2Fk47Ve%2FbtrsrUrTbrj%2FXkzKWBt41TbkMMeJStd4ZK%2Fimg.png)